We have a deep understanding of cybersecurity requirements derived from over 10 years supporting federal cybersecurity efforts at the project and program level. For example, we have documented and assessed security controls, prepared authorization packages, tracked and resolved POA&Ms, reviewed vulnerability scans, implemented multifactor authentication, written privacy policies, and supported security data calls at a variety of agencies including Treasury, HHS, and ED. Our team stands ready to deliver experienced and capable staff to provide the support the IRS needs.
Our approach to cybersecurity emphasizes expert staff, disciplined processes, recognized security frameworks, and customer service to provide full-life cycle support to ensure programs and projects meet all federal and agency security requirements as defined in the IRM 1.1.12.3.
- Expert Staff. Our approach begins with applying expert staff. Cybersecurity is so broad, detailed, and fast-changing, that a mature perspective based on experience is essential to apply federal security guidance effectively. Accordingly, our senior security specialists have a minimum of 15 years of experience, and typically much more. This enables our staff to provide value-added coordination and guidance to programs, projects, and the enterprise.
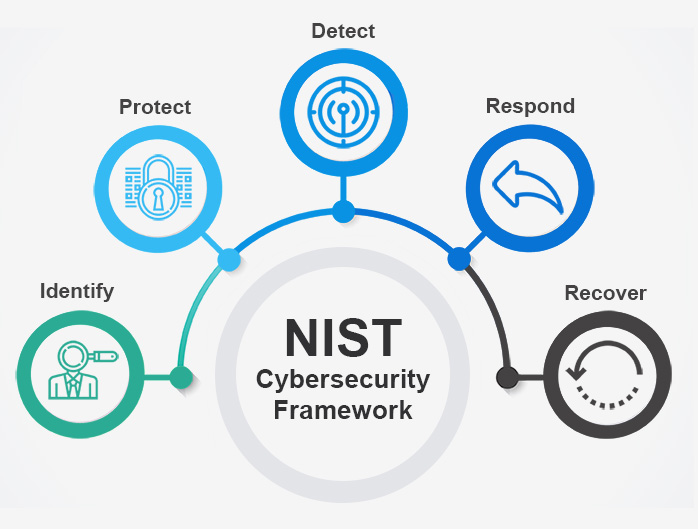
- Disciplined processes and recognized security frameworks. It is evident from experience that bad actors are able to find and exploit the smallest and most obscure security flaws. The cybersecurity chain is only as strong as its weakest link. Accordingly, we use processes and frameworks that ensure comprehensive consideration of security. For example, we use the NIST Cybersecurity Framework to ensure full coverage of various security-related functions during design reviews. Similarly, we use detailed checklists to ensure complete consideration of security at a more detailed level during construction, implementation, and verification.
- Customer service. The final key element of our cybersecurity approach is exemplary customer service. Accordingly, we emphasize customer service by providing the coordination and guidance needed to deliver IT services successfully for organizations and federal agencies. This means staff who are helpful and friendly, which requires both the right capability and attitude.
Success Stories
HHS Grants.gov
BPS provides cybersecurity support at HHS by maintaining a risk register, conducting security testing, performing privacy and security assessments in support of ATOs and managing resulting POA&Ms, coordinating with HHS OCIO in the event of cybersecurity incidents impacting operations, and helping the program maintain an appropriate security posture and controls consistent with NIST cybersecurity guidance.
Department of Education
At ED, we successfully support programs obtaining system ATO by interpreting security requirements; allocating control responsibility, supporting development of security controls, entering control documentation into CSAM, maintaining POA&Ms, and conducting vulnerability scans and reviewing their results.